Key Takeaways
- Reset your account password, sign out of your account from all devices, and enable two-factor authentication to protect your email account from hackers.
- Notify your contacts about the hack and caution them not to act on suspicious emails they may have received.
- Reset passwords for linked accounts, check for suspicious transactions, and rectify any discrepancies you identify in your email account settings.
Have you received complaints from your contacts regarding spam emails originating from your account, or detected other suspicious activity? Your email may have been hacked. Don’t worry; prompt action can help avoid risks to your finances, reputation, and credibility. Here’s what you need to do.
Reset Your Account Password
If you are unable to access your account following a potential hack, the first step is to reset your account password. Even if the hacker hasn’t changed the password, you should change it to prevent them from reusing it to gain access to your account later if they know it.
To change your Gmail account password, you have to update the password for your Google account. Similarly, to alter the Outlook account password, you need to change the password of your Microsoft account. Ensure you complete these steps before proceeding further.
Sign Out of Your Account From All Devices
If your Google or Microsoft account has been compromised by hackers, potentially giving them access to your Gmail or Outlook, they may have already logged into your account on a different device. After you reset your account password, you should sign out of your Google account from all devices where you are currently logged in.
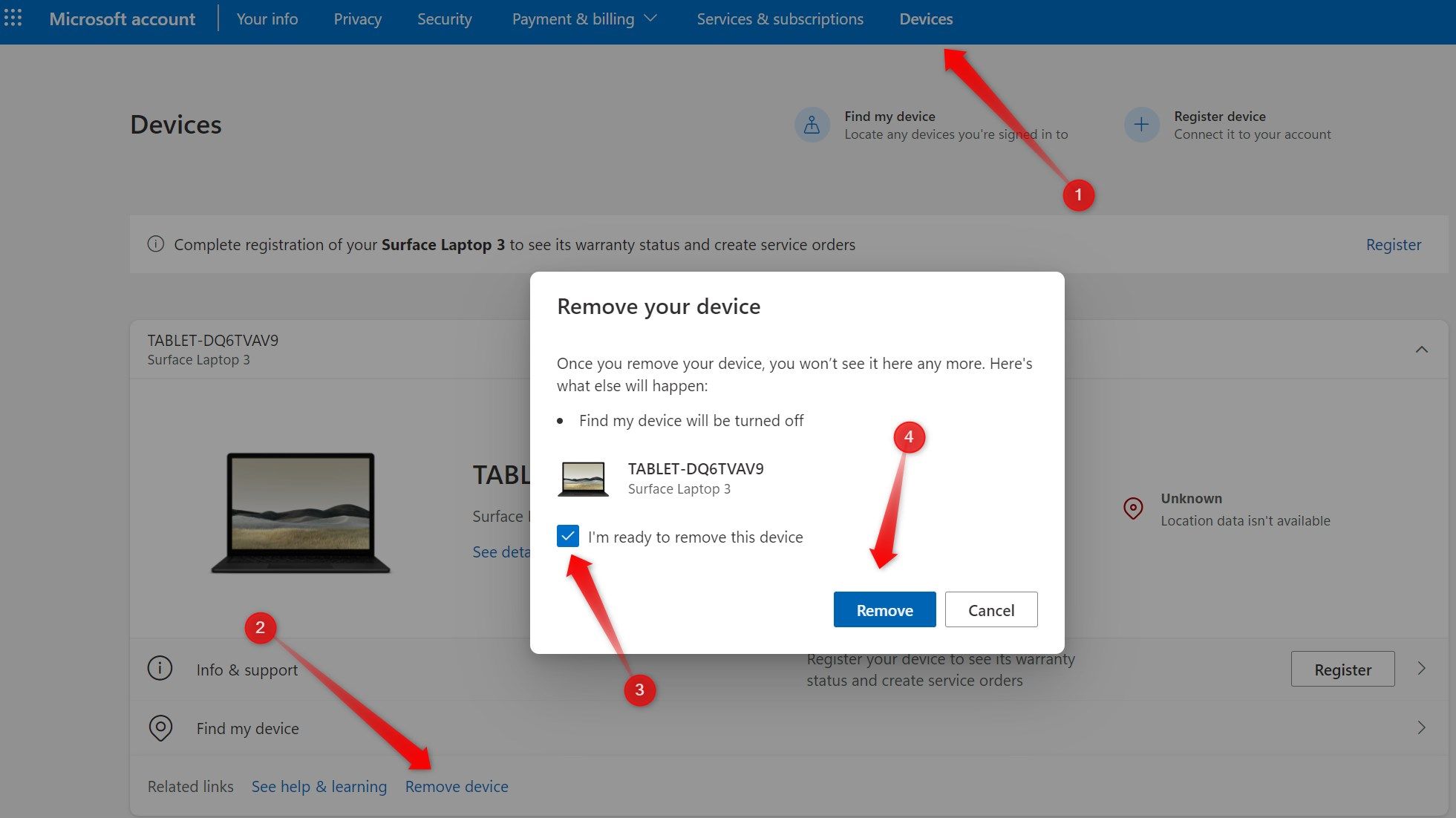
If you’re concerned about a compromised Microsoft account, log in to your account on the Microsoft website and navigate to the “Devices” tab. Identify the unknown device linked to your account, click “Remove Device,” check the box beside “I’m Ready to Remove This Device,” and click the “Remove” button. This step will remove your Microsoft account from the suspicious device.
Afterward, you can log in to your account on your trusted devices using the new password, guaranteeing that only you have access to your account.
Once you successfully log in to your account, your first action should be to compose an email addressing the hack and send it to all of your contacts. In the email, explicitly state that any messages they may have received could be from the hacker who compromised your account and advise them not to act on such emails.
Subsequently, navigate to the Sent folder to review emails sent from your account. Unless the hackers have deleted the sent emails, check them and make a note of unfamiliar contacts that have been contacted from your account. Then, inform these contacts about the security breach and caution them not to act upon the content of the email they have received from your end.
Set Up Two-Factor Authentication
Enabling two-factor authentication (2FA) adds an extra layer of defense against hackers attempting to compromise your account. This security feature requires anyone trying to log in from a new device to confirm their identity through multiple means. So, even if your email account password is exposed, hackers won’t be able to gain unauthorized access.
Set up 2FA for your Google and Microsoft accounts if you haven’t already. This proactive step will prevent hackers from succeeding if they attempt to infiltrate your account a
Reset the Password of Your Linked Accounts
It’s common for hackers to attempt password resets for accounts associated with the compromised email address or those using it for verification. As a precautionary measure, if your compromised email is linked to a secondary email account, reset that password too.
Furthermore, if you see emails about password reset attempts for critical accounts such as banking or social media, immediately reset their passwords. If your email is used for sign-ups on new platforms or websites, reset the passwords for those accounts as well, and if feasible, consider closing those accounts.
Ensure Your Emails Aren’t Being Forwarded
After a hack, hackers may employ a sneaky method to spy on you by adding a forwarding email address to your account, thus diverting your incoming emails to the hacker’s address. Some email clients allow users to set up automatic deletion of forwarded emails. So, if hackers employ this tactic, they could keep you oblivious to surveillance.
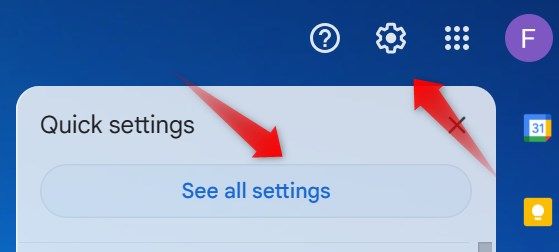
To check this on Gmail, click the gear icon and open “See All Settings.”
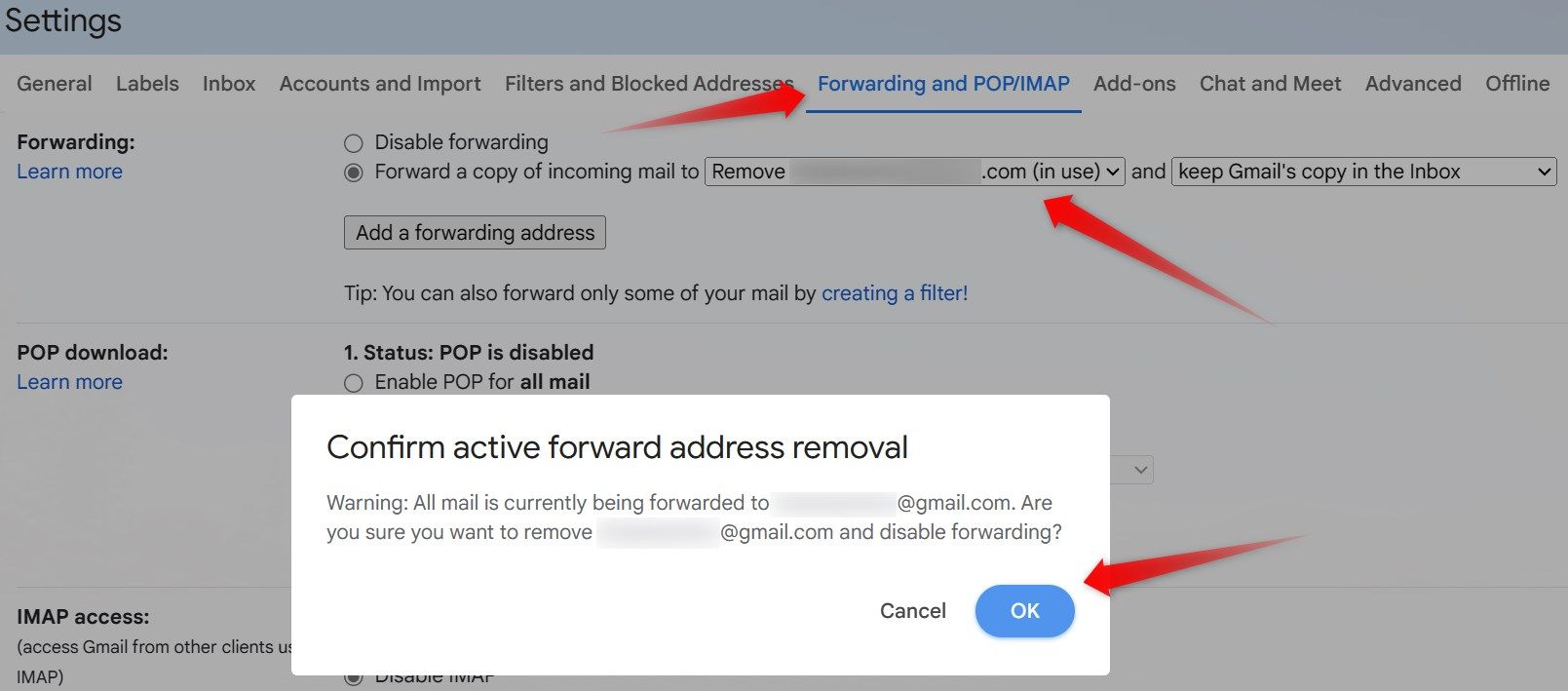
Navigate to the “Forwarding and POP/IMAP” settings, choose “remove <email address>” from the dropdown menu next to “Forward a Copy Of Incoming Mail To,” and confirm by clicking “OK” in the confirmation box.
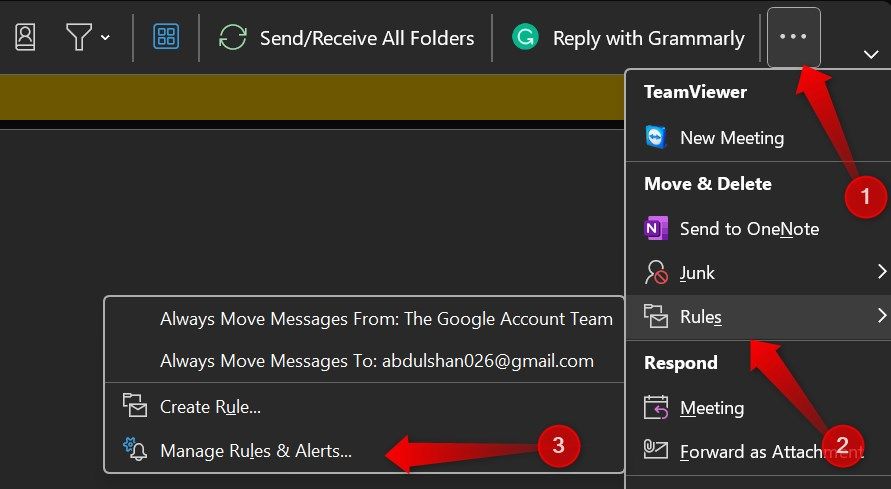
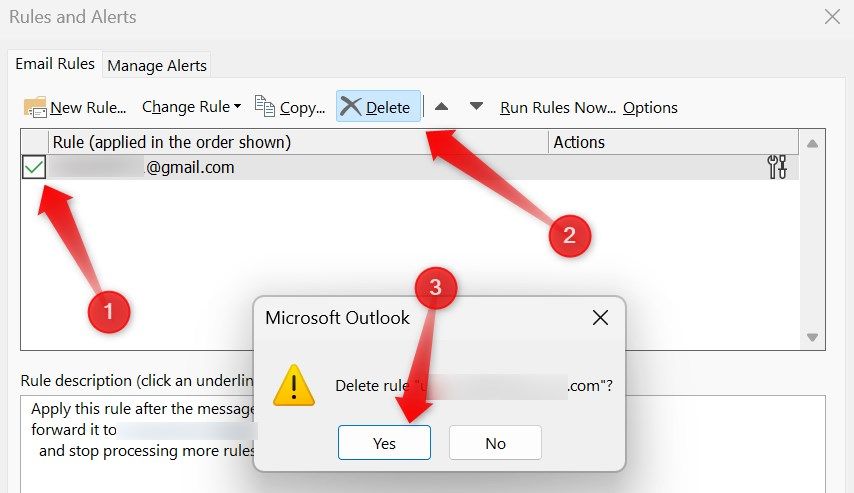
In Outlook, click the three horizontal dots at the ribbon’s extreme right and go to Rules > Manage Rules and Alerts.
Review the rules, and if you spot a new rule forwarding emails to an unknown address, select it and click “Delete.” Confirm the deletion by clicking “Yes” in the popup.
Check for Suspicious Transactions
If you encounter emails reporting suspicious transactions from your bank account or online wallets like Google Wallet, contact the bank or wallet support promptly. Notify them about the hack and inquire about a possible refund. Simultaneously, change the account password of your account.
If you suspect your credit card information has been compromised, request the relevant company to temporarily freeze it. Taking the precautionary measure of temporarily freezing your other bank or wallet accounts online can also be a wise step, particularly if you have concerns regarding the security of your financial accounts.
Check Other Account Settings
Hackers may have manipulated your email account settings to further their malicious intentions even after you’ve regained control of your account. They might whitelist their email address to send phishing spam, create filters diverting essential emails to your spam folder, set confidential emails to auto-delete, and more.
To safeguard against such tricks, meticulously review all settings on your email account and rectify any discrepancies you identify.
With any luck, applying the tips above will help you recover your account and mitigate the potential for serious harm. Time is of the essence; delaying could still expose your privacy to risks. Monitor the activity of your email account for a few days, and if you notice any suspicious behavior, take immediate action to secure your account.
source